In the vast digital landscape, where every click and download comes with potential risks, one threat looms large—Remote Access Trojans (RATs). These silent invaders can compromise your privacy and wreak havoc on your system without you even realizing it. In this guide, we will delve deep into the world of RATs, understanding their insidious nature, and equipping you with the knowledge to detect and eliminate them from your PC.
What is a RAT?
A Remote Access Trojan is a malicious software wielded by attackers to seize complete control over a targeted computer. Often camouflaged as innocuous programs or nestled within phishing emails, RATs disguise their true nature, infiltrating systems undetected.
How do RATs Operate?
Deployed through exploit kits like Metasploit or insidious phishing emails, RATs establish a connection to a command-and-control server. Once in, they transform the host into a puppet, enabling a spectrum of invasive actions.
RAT Capabilities:
| Functionality | Description |
|---|---|
| Monitor User Behavior | Keystroke logging and spyware to observe user activity. |
| Access Confidential Information | Infiltrate and exfiltrate sensitive data. |
| Activate System’s Webcam | Covert video recording capabilities. |
| Take Screenshots | Capture visual snapshots of the user’s environment. |
| Distribute Viruses and Malware | Serve as a launchpad for malicious payloads. |
| Format Drives | Wipe out entire data repositories. |
| Delete, Download, or Alter Files | Manipulate files and file systems at will. |
Detecting Remote Access Trojans
Given their adeptness at evasion, detecting RATs demands vigilance. Keep an eye out for the following signs:
Signs of RAT Infection:
- Failure of Antivirus Program: Frequent crashes or slowdowns may indicate an infection.
- Slow System Performance: Unexplained sluggishness suggests background processes.
- Website Redirects: Constant redirection or unresponsive webpages can be red flags.
- Unidentifiable Files: Any unfamiliar files could be linked to Trojan viruses.
- Operational Webcam: An unexpectedly active webcam indicator light signals intrusion.
How to Detect RAT Virus on Your PC?
Method 1 – Detect Remote Access Trojan Using System.ini
- Open Command Prompt as Admin.
- Execute the command
system.ini. - This will bring up a notepad file containing information about the system.
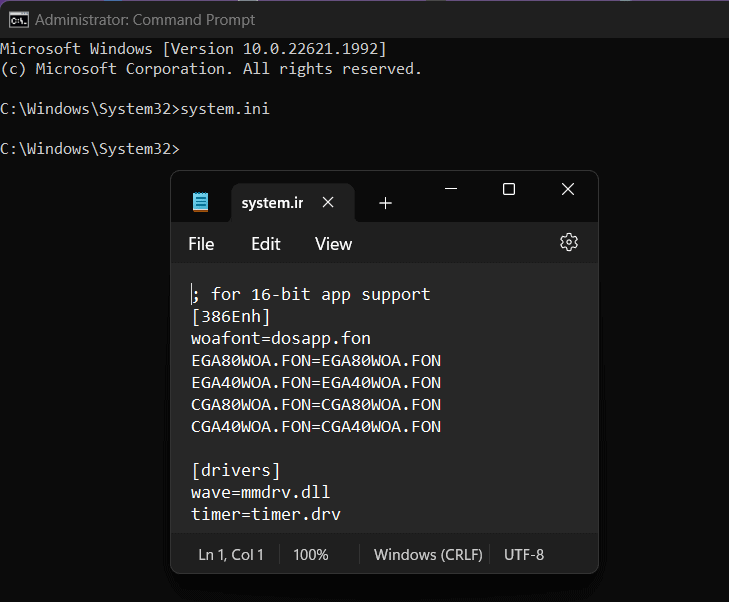
- Check for unusual entries in the Drivers section.
- If you find something odd, someone else is remotely accessing your PC, or there is a RAT malware on your computer.
Method 2 – Detect RAT Virus Using PID of the Process
- Open Command Prompt as Admin.
- Use
netstat -anoto find foreign programs.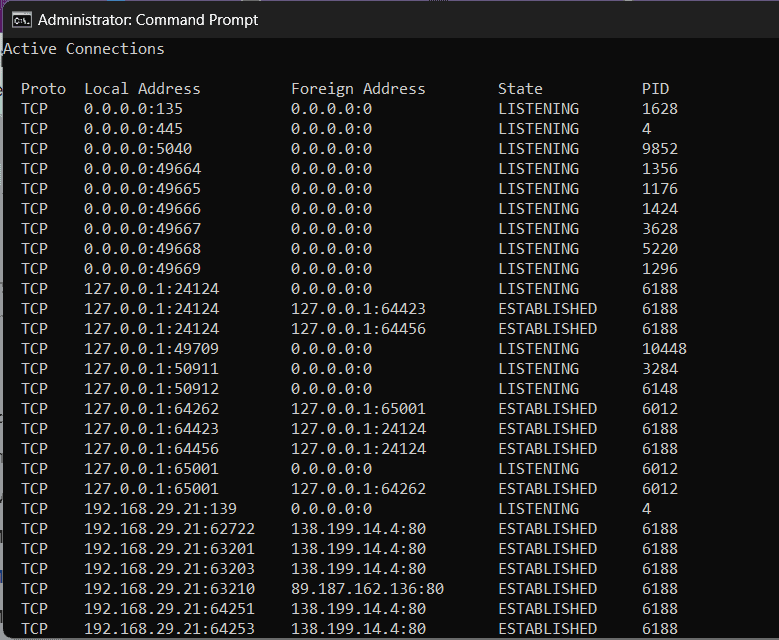
- Match PID in Task Manager to identify malicious programs.
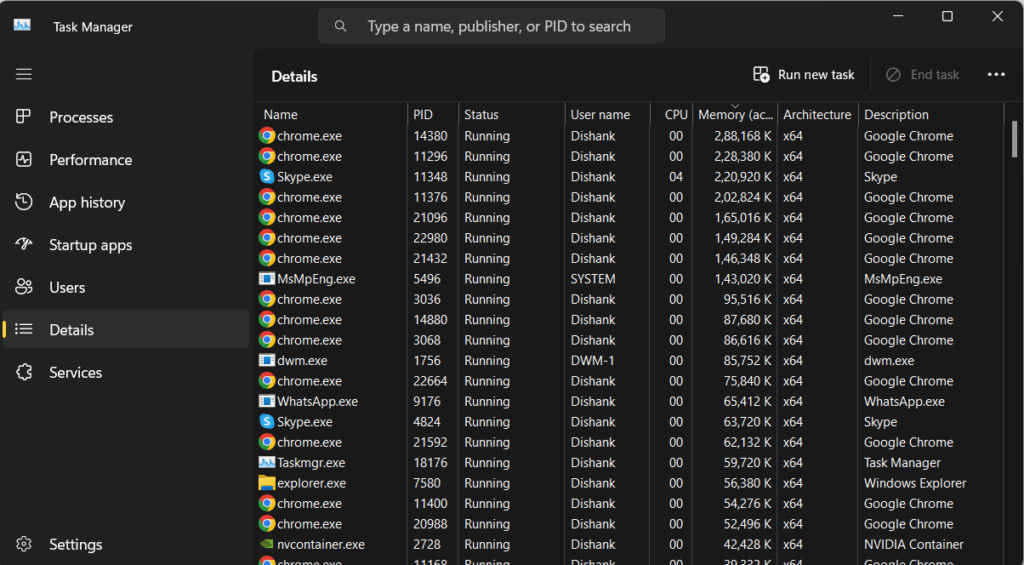
When you match them both, you can identify that program as a malicious file with the potential threat of being a RAT virus.
Method 3 – Use an Antivirus Program
- T9 Antivirus: Real-time protection against RATs.
How to Remove Remote Access Trojan from PC?
- Stop the Malicious Service
- Identify and halt the service.
- Disconnect the Internet Connection
- Weaken the RAT by cutting off remote access.
- Use a Removal Program Like T9 Antivirus
- Download, install, and run a scan with T9 Antivirus.
Stay Safe From the Remote Access Trojan Virus
Prevention Tips:
- Avoid Using Untrusted Sources for Downloading Files
- Protect your system from potential RAT gateways.
- Always Have an Active Security Program like T9 Antivirus
- A vigilant guardian against Trojan infiltrations.
- Never Keep Your Credentials on Your PC without Protection
- Safeguard sensitive information from prying RATs.
- Keep System Definitions & Security Patches Updated
- Fortify your defenses with the latest updates.
- Use a VPN Before Visiting Unknown Sources
- An extra layer of security for your online ventures.
Protecting Against Remote Access Trojans
Guarding against RATs requires a multi-faceted approach. Consider the following proactive measures:
Proactive Measures:
| Defense Strategy | Description |
|---|---|
| Disconnect Devices | Isolate compromised devices from the network. |
| Update Antivirus and Firewalls | Maintain up-to-date security measures. |
| Deploy Multifactor Authentication (MFA) | Add an extra layer of protection with MFA. |
| Avoid Suspicious Links and Attachments | Train users to identify and avoid phishing attempts. |
| Install the Latest Upgrades | Regularly update operating systems for patched security. |
| Use an Intrusion Detection System (IDS) | Monitor network traffic for anomalies and suspicious activity. |
| Employ the Principle of Least Privilege (POLP) | Restrict access to systems and resources to essential levels. |
Frequently Asked Questions
- Q: What is a Remote Access Trojan (RAT)?
- A: A malicious program granting unauthorized remote access to a targeted user’s PC.
- Q: How can I detect a RAT on my computer?
- A: Use methods like inspecting system.ini, identifying processes through PID, or employing antivirus solutions.
- Q: What steps should I take to remove a RAT from my PC?
- A: Stop the malicious service, disconnect from the internet, and use a reliable antivirus program like T9 Antivirus.
- Q: Are there preventive measures to avoid RAT infections?
- A: Yes, avoid untrusted sources, use active security programs, secure your credentials, keep your system updated, and use a VPN for added protection.
- Q: Which antivirus program is recommended for RAT detection?
- A: T9 Antivirus is recommended for its dedicated real-time shields.
Conclusion
In the ever-evolving digital landscape, staying one step ahead of threats like RATs is paramount. By understanding their modus operandi, detecting their presence, and efficiently removing them from your system, you can ensure a safer online experience. Remember, vigilance is your best defense against the invisible invaders.